Background about this Project
This post is about how to reverse and modify the simple Android Dice Roller! app.
The app was randomly chosen by me, I wanted to start with something simple, so:
- there are no signature checks in place
- there is no packed library involved
Before you start
always check, if you can decompile, compile, sign, install and lunch the app, some apps wont run with a changed signature, even if you don’t change anything
The app roles one or more dices and display the user a random result. I wanted to try if I can manipulate this.
How to start
First, we download our target APK from an external play store source: https://apkcombo.com/de/dice/com.harryfo.dice/
We can also extract installed apps from our device, but this will sometimes result in split apps, which involves a few more steps (you need to sign them too)
Find the entry Point
We start with some static analyses and try to find the main activity by open the APK in Jadx-Gui and checking the AndroidManifest.xml for the main activity
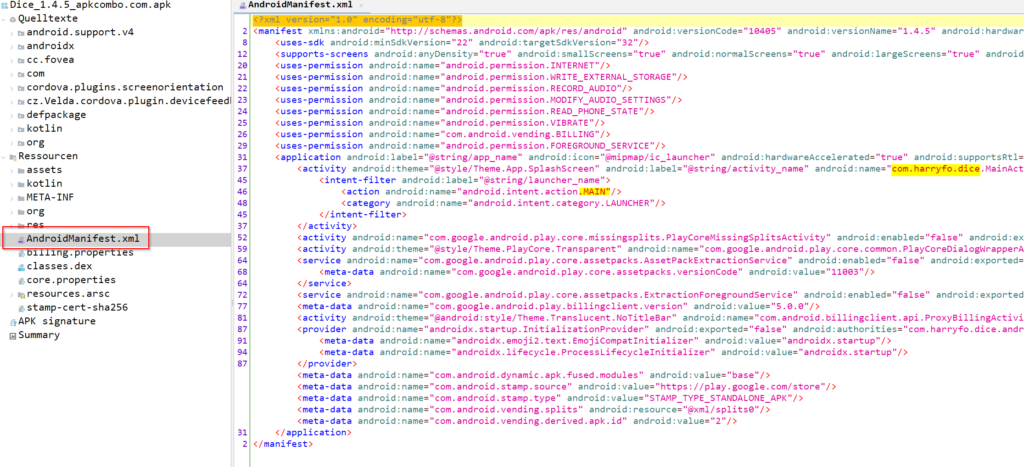
As we can see, it loads the class MainActivity in the com.harryfo.dice namespace. So lets investigate this activity
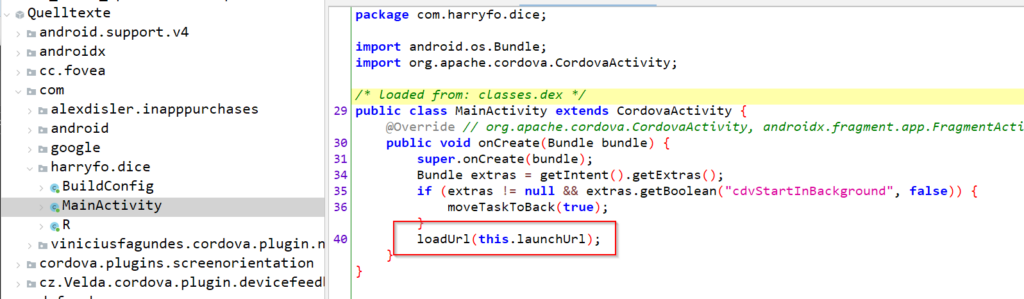
We can see that method just calls a loadUrl function, which seems a little bit weird in the first moment.
Setup for dynamic Analyses
So its time to perform some dynamic analyses and check if we can figure out what URL the app is calling. For this we are using a Android Emulator and Frida.
There are a few things which we need to setup, take a look at Firda Setup. As Emulator, we are using LDPlayer, make sure to enable ADB and root in the Emulator.
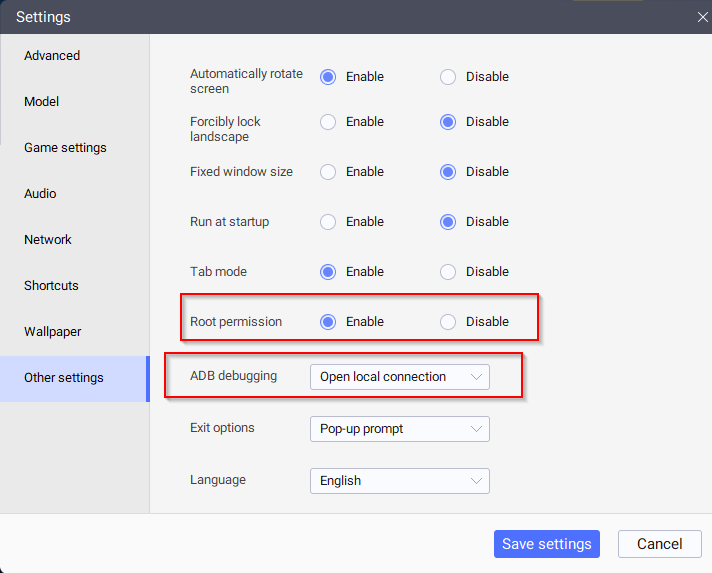
Make sure you have the Frida server running, next we are going to connect to the Frida server, retrieve the Emulator ID and the dice package name
adb devices
adb shell "pm list packages | grep dice"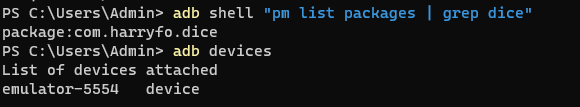
Connect to it and spawn the dice application
frida -D emulator-5554 -f com.harryfo.dice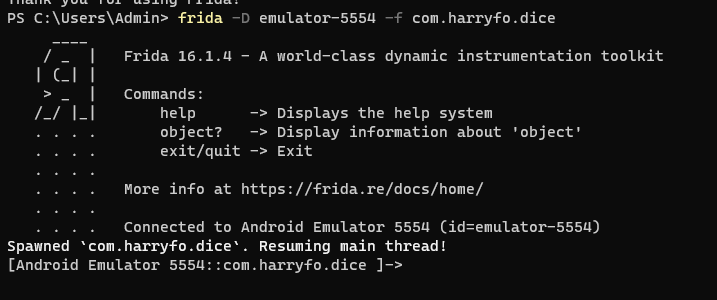
The application should now be started on your emulator.
Trace the action
Next we want to trace our spotted method, for this we can use frida-trace
frida-trace -U -j '*!loadUrl' -f com.harryfo.diceThe application will start and we can see that the application is calling a index.html on localhost.
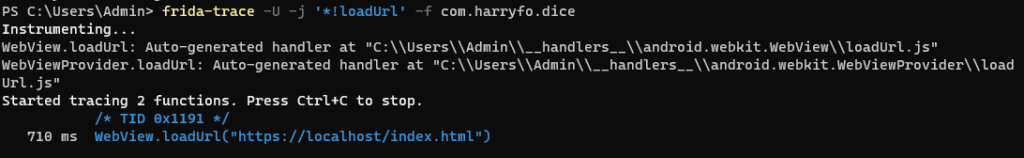
Find the target
We will switch back to our source code and search for the index.html
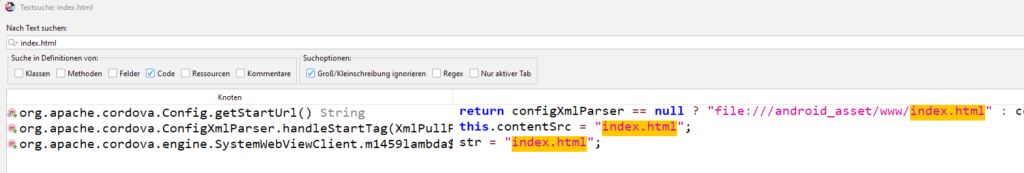
As we can see, there is a index.html in the resource/asset/www folder
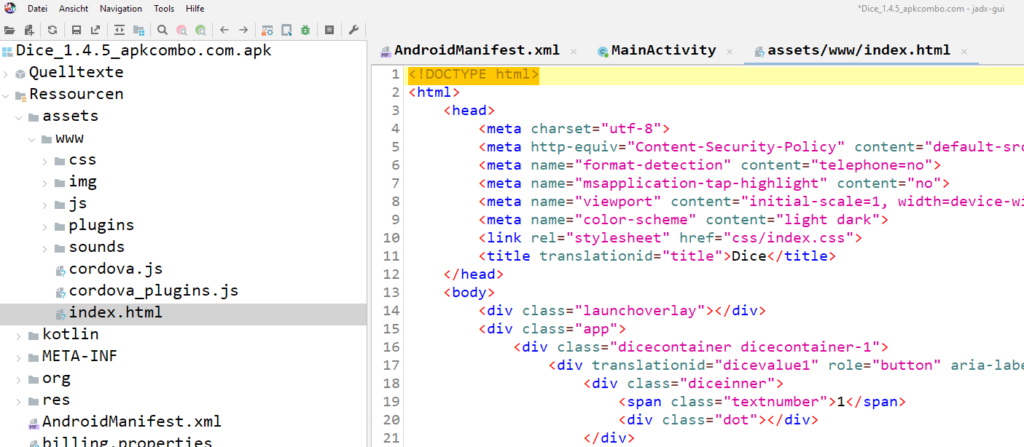
This is exactly what our application looks like, so it seems the app just loads a website and performs all actions in HTML/JS. By looking further in the source code we can find that the page is loading a index.js

If we look at this JS file we can see, that here the dice rolling will be done, after some more JS code investigation we can find our target function which seems to calculate our dice result.
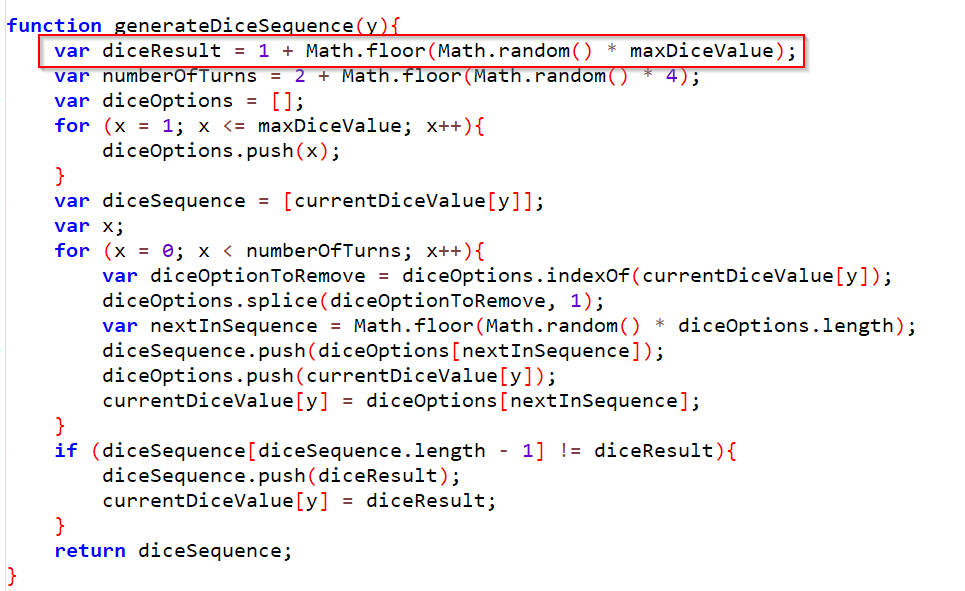
Now as we know what we need to modify, it’s time to patch our application
Decompile the APK
There are many different ways to do this, one of the simplest is to use the APKTool-Gui, so we just need to give them the path to our target apk and hit „Decompile“
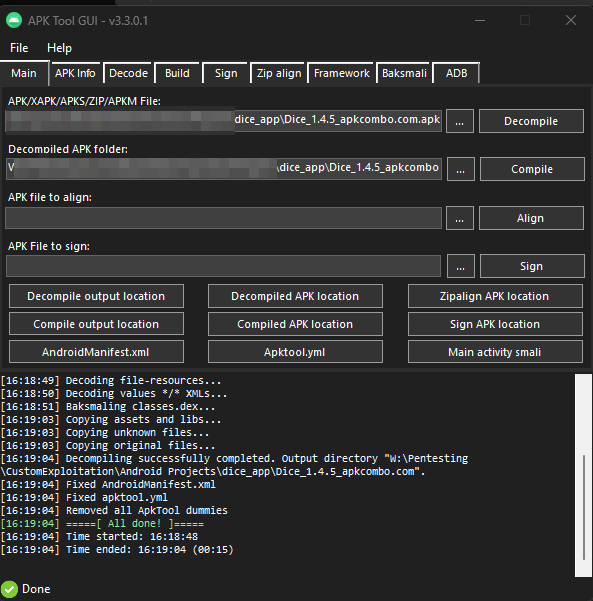
This will give us a folder, where we can find our index.js \Dice_1.4.5_apkcombo.com\assets\www\js\index.js
I modified the line that the role will always give as a 6 and also added a little signature into the app

Compile and Install
Next we only need to hit the „Compile“ Button in the APK Tool, this will give use Dice_1.4.5_apkcombo.com signed.apk which we can install by drag and drop to our emulator.
After clicking the dice, we can notice that we will always get some sixes.
In the settings, we can turn on the „show total“ option
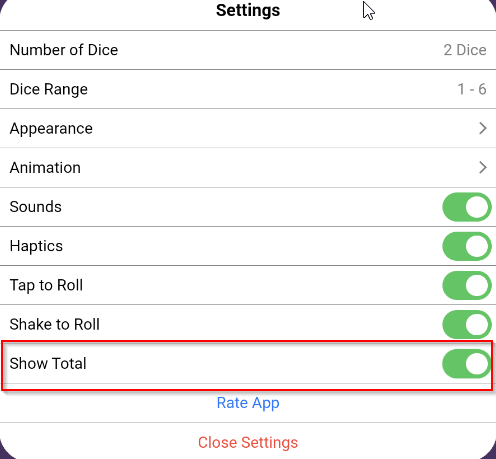
and we can see our final result

Bonus: Hooking
With Frida it is also possible to overwrite methods and values on the fly, without recompiling the app. As this app only loads a website, we can try to overwrite the loading site.
For this we need to write a little Frida script which overwrites the loadURL method of the class org.apache.cordova.CordovaActivity to use our desired value
Java.perform(function() {
var webView = Java.use("org.apache.cordova.CordovaActivity");
webView.loadUrl.overload("java.lang.String").implementation = function(url) {
var file_path = 'https://secure77.de/index.html'; // path to file to load on webview
this.loadUrl.overload("java.lang.String").call(this, file_path);
}
});we can then use Frida and start the app with our script, and load our defined website
frida -D emulator-5554 -l .\url.js -f com.harryfo.dice
Outro
This was pretty simple, in my next post I will write about how to patch a unity game.
