gMSA Passwords
Doing one of the recent HTB Boxes i came across the tool https://nettools.net and learned how you can retrieve gMSA passwords with it: https://nettools.net/howto-retrieving-gmsa-password-details/
Additional to the howto from NetTools you can change the encoding for the desired attribute to only retrieve the current password
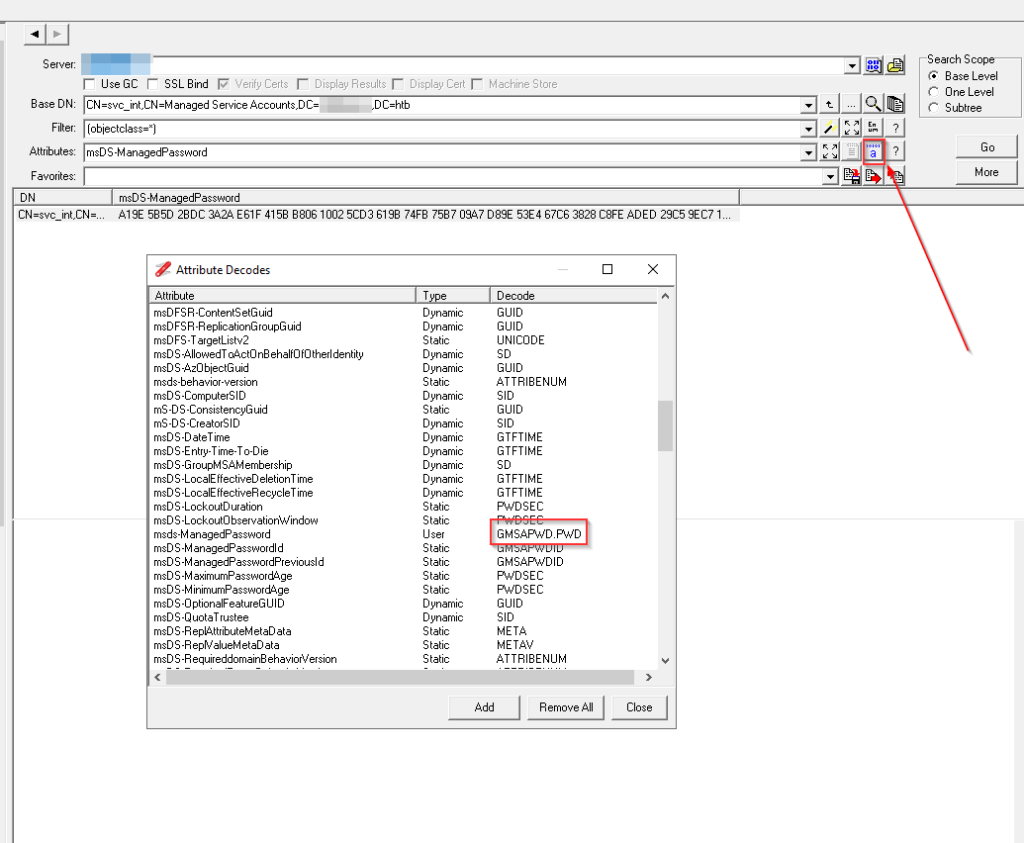
this will print you only the current password as hex for the user
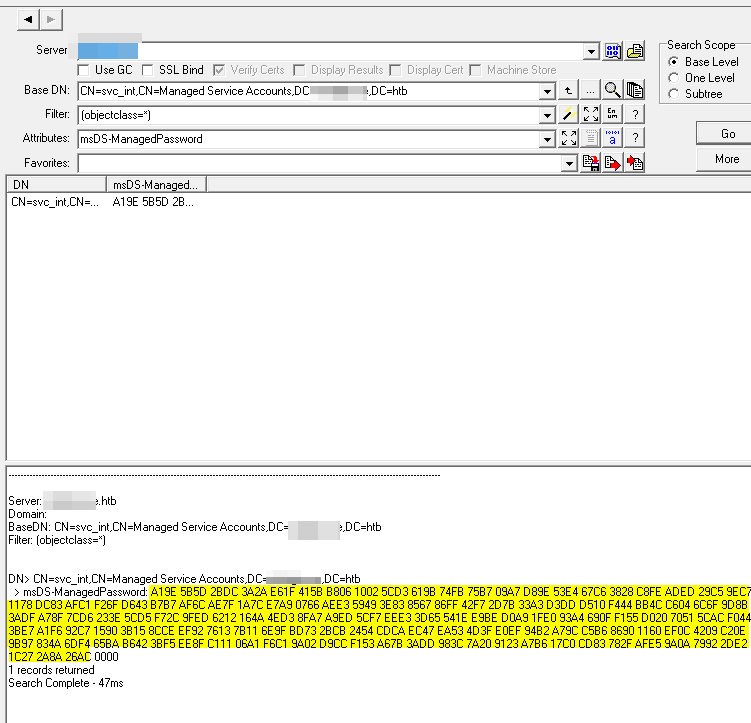
Its the same as opening the AD Properties and selecting the hex and copy paste it out of it
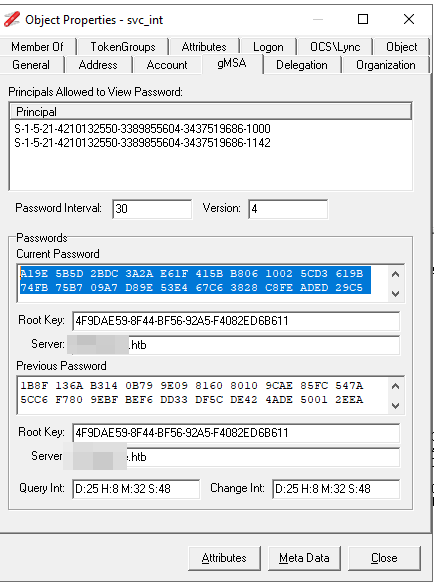
NetTools also provide a way to retrieve the clear text password. Just right click into the current password field and select „copy password“.
This will give you the following password:

You can paste this to the windows login prompt but unfortunately i was not able to use this in linux terminal related tools.
Googling more about gMSA passwords i found this handy tool: https://github.com/micahvandeusen/gMSADumper
With this it is easy possible to retrieve the gMSA passwords. The tool provide the password as MD4 / NT Hash, so you can use it for pass-the-hash attacks.
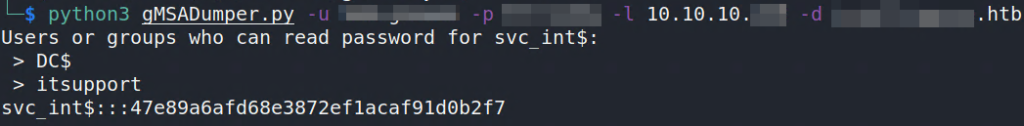
I was curious if there is a way to convert the dump from NetTools to archive the same result / hash. And it is.
First of all i started to dig into the gMSADumper.py and print me out the data before the hashing occurs.
[snip]
data = entry['msDS-ManagedPassword'].raw_values[0]
blob = MSDS_MANAGEDPASSWORD_BLOB()
blob.fromString(data)
test = blob['CurrentPassword'][:-2]
print('\n Current Password raw: ')
print(test)
print('\n Current Password hex')
print(binascii.hexlify(test))
print('\n')
hash = MD4.new ()
hash.update (blob['CurrentPassword'][:-2])
passwd = binascii.hexlify(hash.digest()).decode("utf-8")
userpass = sam + ':::' + passwd
print(userpass)Output
Current Password raw:
b"\x9e\xa1][\xdc+*:\x1f\xe6[A\x06\xb8\x02\x10\xd3\\\x9ba\xfbt\xb7u\xa7\t\x9e\xd8\xe4S\xc6g(8\xfe\xc8\xed\xad\xc5)\xc7\x9ex\x11\x83\xdc\xc1\xafo\xf2C\xd6\xb7\xb7l\xaf\x7f\xae|\x1a\xa9\xe7f\x07\xe3\xaeIY\x83>g\x85\xff\x86\xf7B{-\xa33\xdd\xd3\x10\xd5D\xf4L\xbb\x04\xc6ol\x8b\x9d\xdf:\x8f\xa7\xd6|>#\xd5\\,\xf7\xed\x9f\x12bJ\x16\xd3N\xa7\x8f\xed\xa9\xf7\\\xe3\xeee=\x1eT\xbe\xe9\xa9\xd0\xe0\x1f\xa4\x93\x0fiU\xf1 \xd0Qp\xac\\D\xf0\xe7;\xf6\xa1\xc7\x92\x90\x15\x15;\xce\x8c\x92\xef\x13v\x11{\x9fns\xbd\xcb+T$\xca\xcdG\xecS\xea?M\xef\xe0\xb2\x94\x9c\xa7\xb6\xc5\x90\x86`\x11\x0c\xef\tB\x0e\xc2\x97\x9bJ\x83\xf4m\xbaeB\xb6\xf5;\x8f\xee\x11\xc1\xa1\x06\xc1\xf6\x02\x9a\xcc\xd9S\xf1{\xa6\xdd:<\x98 z#\x91\xb6\xa7\xc0\x17\x83\xcd/x\xe5\xaf\n\x9a\x92y\xe2-'\x1c\x8a*\xac&"
Current Password hex:
b'9ea15d5bdc2b2a3a1fe65b4106b80210d35c9b61fb74b775a7099ed8e453c6672838fec8edadc529c79e781183dcc1af6ff243d6b7b76caf7fae7c1aa9e76607e3ae4959833e6785ff86f7427b2da333ddd310d544f44cbb04c66f6c8b9ddf3a8fa7d67c3e23d55c2cf7ed9f12624a16d34ea78feda9f75ce3ee653d1e54bee9a9d0e01fa4930f6955f120d05170ac5c44f0e73bf6a1c7929015153bce8c92ef1376117b9f6e73bdcb2b5424cacd47ec53ea3f4defe0b2949ca7b6c5908660110cef09420ec2979b4a83f46dba6542b6f53b8fee11c1a106c1f6029accd953f17ba6dd3a3c98207a2391b6a7c01783cd2f78e5af0a9a9279e22d271c8a2aac26'
svc_int$:::47e89a6afd68e3872ef1acaf91d0b2f7To get a better overview to compare, i replaced the white spaces from the NetTools dump and also lowercased the chars with cyberchef.
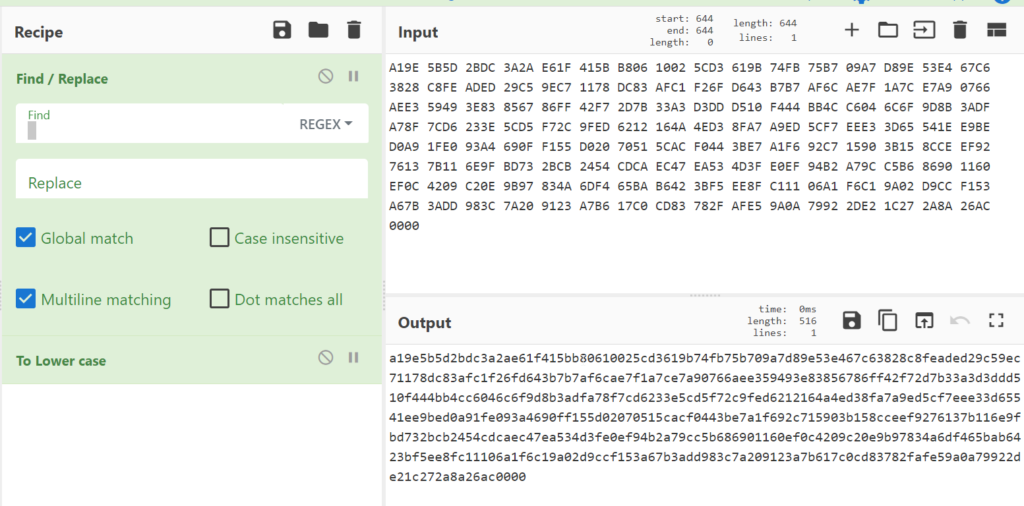
As we can see now, the hex output from gMSADumper.py looks similar to the output from NetTools. But something is still different.
gMSADumper:
9ea15d5bdc2b2a3a1fe65b4106b80210d35c9b61fb74b775a7099ed8e453c6672838fec8edadc529c79e781183dcc1af6ff243d6b7b76caf7fae7c1aa9e76607e3ae4959833e6785ff86f7427b2da333ddd310d544f44cbb04c66f6c8b9ddf3a8fa7d67c3e23d55c2cf7ed9f12624a16d34ea78feda9f75ce3ee653d1e54bee9a9d0e01fa4930f6955f120d05170ac5c44f0e73bf6a1c7929015153bce8c92ef1376117b9f6e73bdcb2b5424cacd47ec53ea3f4defe0b2949ca7b6c5908660110cef09420ec2979b4a83f46dba6542b6f53b8fee11c1a106c1f6029accd953f17ba6dd3a3c98207a2391b6a7c01783cd2f78e5af0a9a9279e22d271c8a2aac26NetTools:
a19e5b5d2bdc3a2ae61f415bb80610025cd3619b74fb75b709a7d89e53e467c63828c8feaded29c59ec71178dc83afc1f26fd643b7b7af6cae7f1a7ce7a90766aee359493e83856786ff42f72d7b33a3d3ddd510f444bb4cc6046c6f9d8b3adfa78f7cd6233e5cd5f72c9fed6212164a4ed38fa7a9ed5cf7eee33d65541ee9bed0a91fe093a4690ff155d02070515cacf0443be7a1f692c715903b158cceef9276137b116e9fbd732bcb2454cdcaec47ea534d3fe0ef94b2a79cc5b686901160ef0c4209c20e9b97834a6df465bab6423bf5ee8fc11106a1f6c19a02d9ccf153a67b3add983c7a209123a7b617c0cd83782fafe59a0a79922de21c272a8a26ac0000Everybody who have a little bit knowledge about assembly or hex, should see the difference and recognize it is because of the endianness. I tried to change the endianness with cyberchef
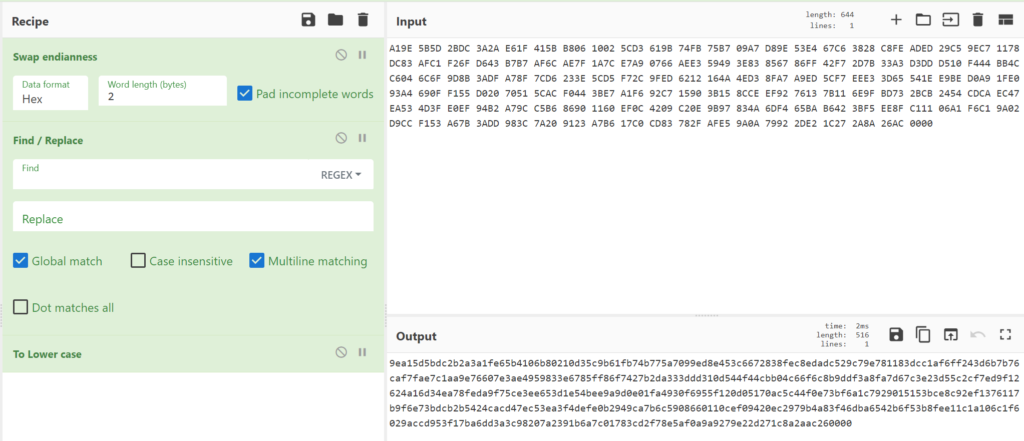
Yes! Now also delete the trailing zero bytes (0000) and we have the exact hex data as gMSADumper and after converting the hex to binary data we can create the hash out of it.
I wrote a little python script to automate the steps: https://github.com/secure-77/NetTools_gMSA_Converter
python3 Convert_gMSA.py -i 'A19E 5B5D 2BDC 3A2A E61F 415B B806 1002 5CD3 619B 74FB 75B7 09A7 D89E 53E4 67C6 3828 C8FE ADED 29C5 9EC7 1178 DC83 AFC1 F26F D643 B7B7 AF6C AE7F 1A7C E7A9 0766 AEE3 5949 3E83 8567 86FF 42F7 2D7B 33A3 D3DD D510 F444 BB4C C604 6C6F 9D8B 3ADF A78F 7CD6 233E 5CD5 F72C 9FED 6212 164A 4ED3 8FA7 A9ED 5CF7 EEE3 3D65 541E E9BE D0A9 1FE0 93A4 690F F155 D020 7051 5CAC F044 3BE7 A1F6 92C7 1590 3B15 8CCE EF92 7613 7B11 6E9F BD73 2BCB 2454 CDCA EC47 EA53 4D3F E0EF 94B2 A79C C5B6 8690 1160 EF0C 4209 C20E 9B97 834A 6DF4 65BA B642 3BF5 EE8F C111 06A1 F6C1 9A02 D9CC F153 A67B 3ADD 983C 7A20 9123 A7B6 17C0 CD83 782F AFE5 9A0A 7992 2DE2 1C27 2A8A 26AC'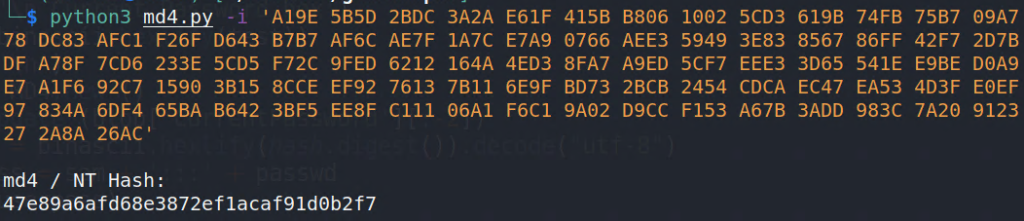
As we can see we get the same hash as with gMSADumper

Further helpful information about gMSA Passwords:
https://cube0x0.github.io/Relaying-for-gMSA/
https://www.dsinternals.com/en/retrieving-cleartext-gmsa-passwords-from-active-directory/

Hi,
Some additional info on the GMSA password.
The default output for the attribute in NetTools uses the decode type GMSAPWD.PWD which decode the data structure and displays the password as a unicode hex dump. This is the actual password and there is no additional decoding required and if the password is copied from the AD Properties dialog, you can paste the password directly from the clipboard into logon prompt or command prompt.
If you want to get a byte dump of the password, using the LDAP Search option and use the following in the attribute field, msDS-ManagedPassword;bin and this will display the byte based dump. However, this will also display the data structure of the attribute. I’ll look at adding specific byte based output in the next version.
Gary.
Hey Gary,
Thanks for your comment and the additional info!
Great tool by the way 👍
BR,
Sec77
NetTools v1.30.1 Beta now includes the Decode Type GMSAPWD.PWD_B and GMSAPWD.PPWD_B to provide the byte based hex output of the GMSA passwords.
Enjoy.
Gary.